Massive data breaches at Target and Home Depot. Edward Snowden and WikiLeaks. Anonymous a war with ISIS. Whether it’s the outright fraud of people stealing information from networks or the type of cyber vigilantism espoused by information leaks or “hacktivist” groups, cybercrime is all over the news.
But what does it all cost?
As much as $65 million per year for some organizations in the U.S., apparently.
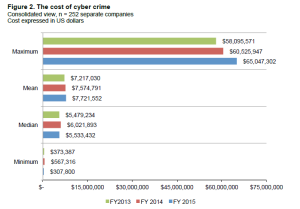
So said the recently released 2015 Cost of Cyber Crime Study, produced by research house Ponemon Institute. The range for this year spanned from $1.9 million to that $65 million number—an average of $15 million per organization. The study also indicates that since 2009, the average per-organization cost of cybercrime has risen 82 percent.
Per HP Enterprise study
Given the fact that this study was also an advertisement for sponsored by HP Enterprise Security, the veracity of the survey methods may be debatable, but it’s not difficult to believe the number is significant—even if the data is not exact.
I was hoping to cross-reference by looking at other studies, but the only other one I could find that wasn’t outrageously expensive was not put together by an independent analyst firm either. It came from Intel Security brand McAfee and estimated the global cost of cybercrime to be between $375 billion and $575 billion.
Apparently the best we can do globally is to get within $200 billion of an actual value. (Students everywhere wish we were afforded that kind of margin for error.)
While the cost per organization in the U.S. and the total aggregate cost to the global economy are completely different, cybercrime is a huge issue with massive economic ramifications however you slice it.
Despite this dearth of objective information, businesses of all sizes acknowledge that cybercrime is a growing concern. It’s only logical in today’s digital era that as networks continue to advance and become more pervasive, threats do as well. Unfortunately, the threats have become more advanced than the network safeguards developed to keep them out.
The old model required a threat to be defined in order for a program to find and neutralize it, but as malicious code and network intrusion techniques have become more advanced, threats embed themselves into networks and simply reside undetected. Once they’re activated and recognizable as a defined threat, it’s too late for the threat to be neutralized before data is stolen.
Advanced techniques are more proactive in nature and are able to root out some of these dormant threats and patch vulnerabilities, but the arms race between cybersecurity professionals and hacker collectives is on. And the growing costs associated with this ongoing battle are not likely to slow down anytime soon.